Endpoint Protection
Secure every device with built-in endpoint protection
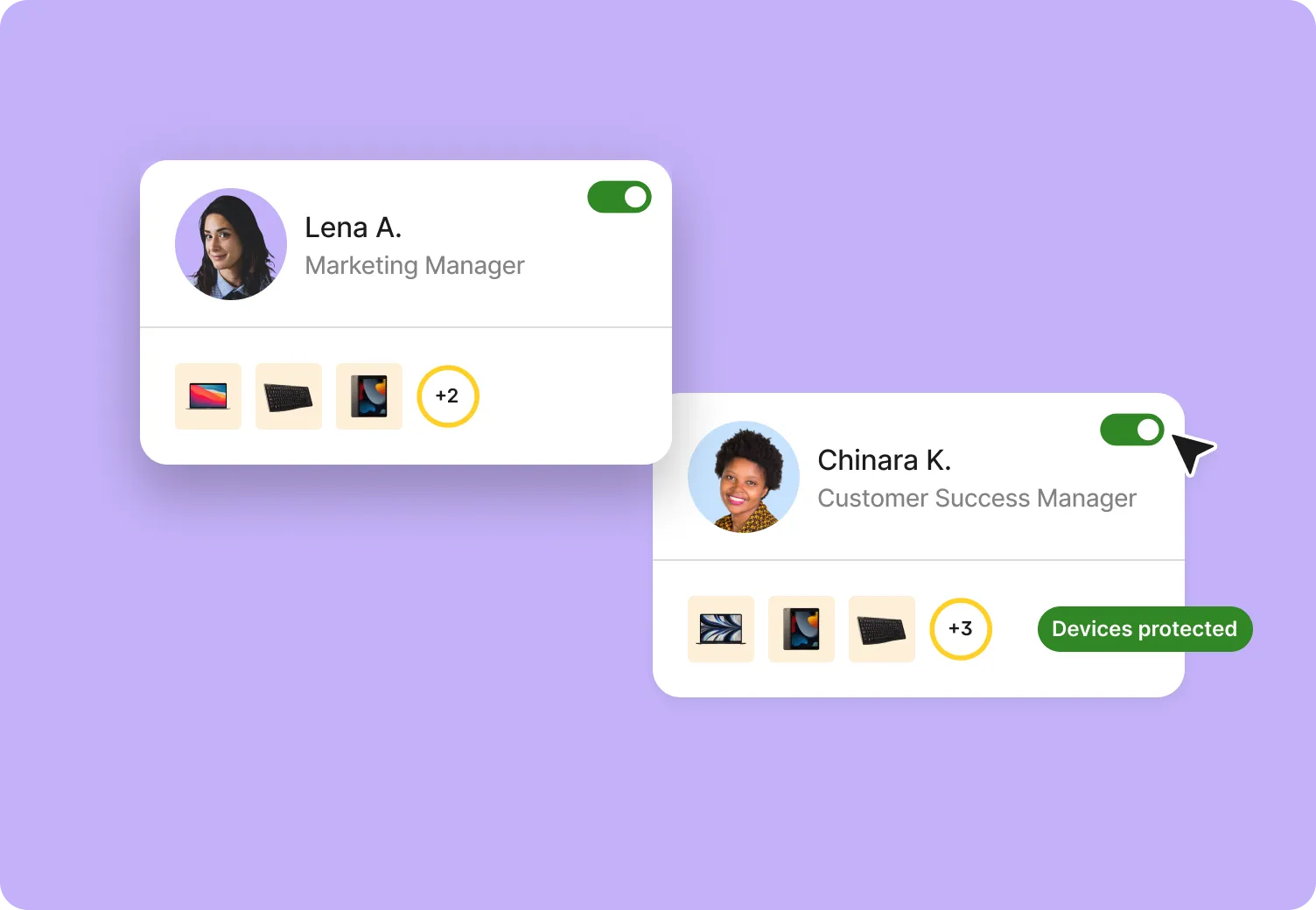
Deel IT automatically applies endpoint protection to your device fleet. From the moment they are shipped, security policies are enforced through active use, recovery, and retirement. IT teams maintain consistent protection everywhere employees work, without manual setup or extra tools.

Cyber security protection
Prevent costly data breaches before they start
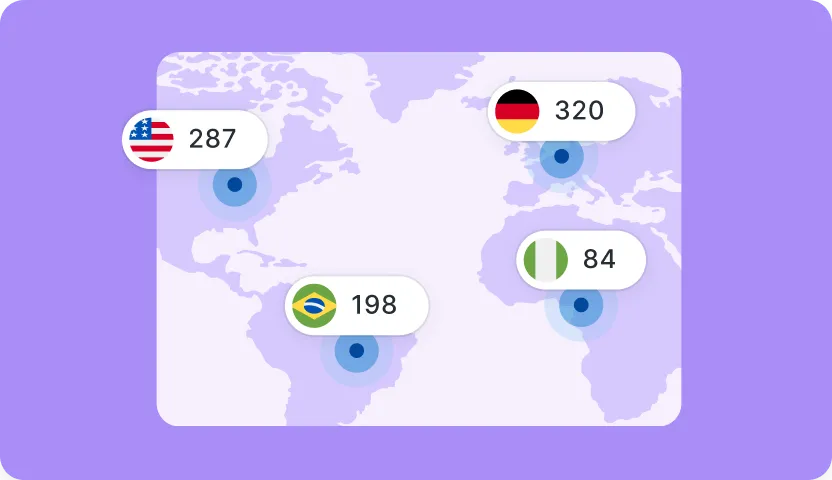
A single scam link exposes your company to major data loss and compliance risks. Proactive protection is applied consistently across laptops and other supported devices, detecting and containing threats during daily use before they ever reach your teams.

Comprehensive endpoint protection
One system to protect every device
Always-on endpoint protection
Endpoint protection runs continuously across managed devices, detecting and containing threats in real time without manual intervention.
FAQs
How does Endpoint Protection affect device performance?
Endpoint Protection is designed to run quietly in the background. It operates with minimal impact on device performance, so employees can work normally without interruptions, pop-ups, or frequent reboots.
What types of devices are supported?
Endpoint Protection applies to supported laptops and other managed devices across major operating systems. Coverage depends on device type and configuration, and IT teams retain visibility into which devices are protected.
How are risks and alerts prioritized?
Security signals are prioritized based on severity and impact. Only critical risks surface for action, helping IT teams focus on what matters most instead of sorting through low-value alerts.
Can IT enforce security restrictions on devices?
Yes. IT teams can apply security restrictions to managed devices to prevent risky actions. These restrictions are enforced automatically based on policy, reducing the chance of incidents without manual oversight.
How does Endpoint Protection scale as teams grow?
Protection scales automatically as devices are added to your fleet. IT teams can maintain consistent coverage and support without increasing manual workload or adding new tools.
Is Endpoint Protection managed separately from other Deel IT products?
No. Endpoint Protection is managed within Deel IT, alongside other device-related workflows. This helps keep device security consistent and visible as part of the broader IT operating model.
How is Deel different from standalone endpoint security tools?
Standalone security tools protect devices in isolation. Deel ties endpoint protection to device ownership, user identity, and IT workflows—giving teams better visibility, faster response, and fewer gaps across a global fleet.
Resources to get you started
We’ve poured our expertise into a series of thoughtfully crafted, easy-to-follow guides, blogs, and webinars for all business sizes.

Everything EOR: A Guide to Employer of Record

The Business Case for Global Hiring

Employer of Record RFP Template
Deel makes growing remote and international teams effortless
150+
countries
40,000+
customers
$20B+
compliantly processed global payroll
90+
NPS for enterprise customers